Image: Motherboard
Hacking. Disinformation. Surveillance. CYBER is Motherboard's podcast and reporting on the dark underbelly of the internet.
Advertisement
Do you have any more information on these ransomware actors? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, or email joseph.cox@vice.com.
Advertisement
Advertisement
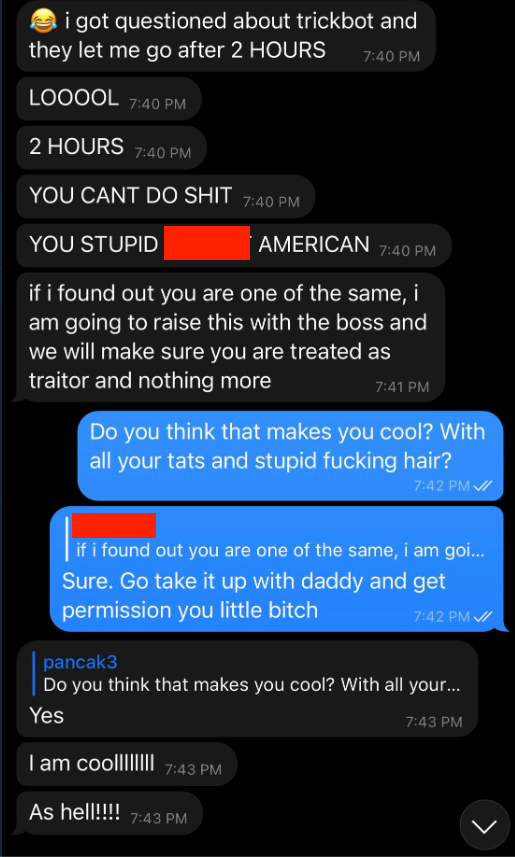
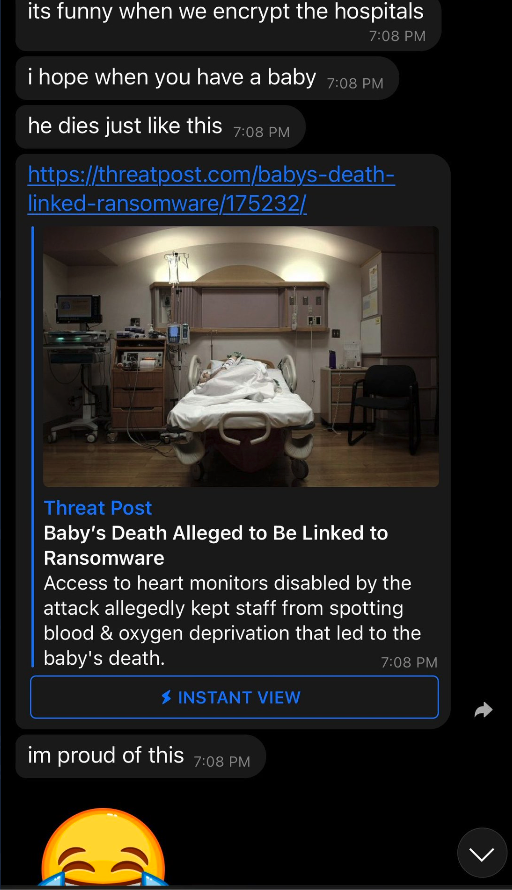
One of the messages Pancak3 said was sent to them. Image: Motherboard.
Advertisement