Image: Cathryn Virginia
Hacking. Disinformation. Surveillance. CYBER is Motherboard's podcast and reporting on the dark underbelly of the internet.
Advertisement
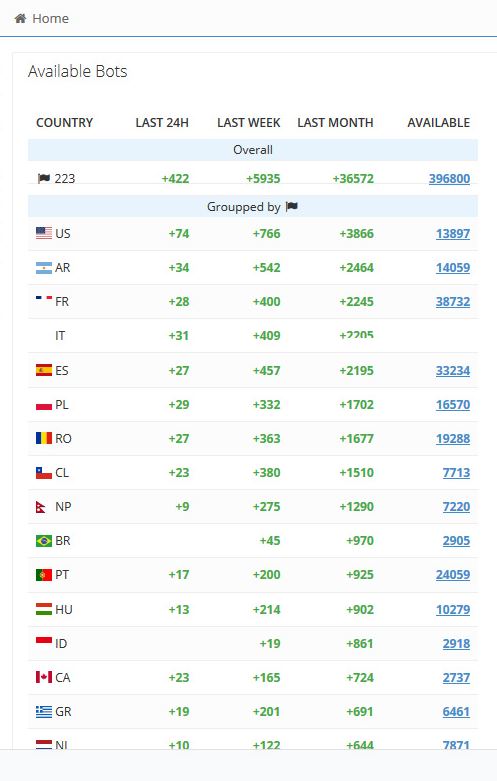
A handful of cybersecurity companies and trade publications have covered the site in the past few years. But its alleged link to a high profile breach demonstrates its increasing relevance in the digital underground.Cookies are small files stored on your computer that can hold all sorts of information. Sometimes they can be used by advertising firms to track browsing activity from site to site; other times they're used for storing login details and keeping you logged into different websites. On Genesis, criminals don't just buy one cookie; they buy exclusive access to a "bot," a compromised computer that is part of a botnet which could contain any number of login details. But more importantly, Genesis also lets customers essentially recreate a one-to-one replica of that victim's browser, with their cookies and device fingerprints intact.Have you used data from Genesis Market in a hack? Do you know anything else about the site? We’d love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
Advertisement
A screenshot of a bot containing Slack credentials. Image: shared by Gracey-McMinn, redactions by Motherboard.
Advertisement
Advertisement

