Image: Roblox
A hacker bribed a Roblox worker to gain access to the back end customer support panel of the massively popular online video game, giving them the ability to lookup personal information on over 100 million active monthly users and grant virtual in-game currency.With this access, the hacker could see users' email address, as well as change passwords, remove two-factor authentication from their accounts, ban users, and more, according to the hacker and screenshots of the internal system. The screenshots shared with Motherboard include the personal information of some of the most high profile users on the platform.The hacker could have looked up information on many users, although it appears they limited their actions to a handful of accounts. The news highlights not only the risk of insiders at companies exploiting their access to user data, but, with Roblox catering to a large audience of minors, how hackers may access the data of children."I did this only to prove a point to them," the hacker told Motherboard in an online chat. Motherboard granted the hacker anonymity to speak more candidly about a criminal incident."Roblox’s mission is to bring the world together through play. We enable anyone to imagine, create, and have fun with friends as they explore millions of immersive 3D experiences, all built by a global community of developers," the company's corporate website reads.The hacker shared a cache of screenshots of the customer support panel containing Roblox user data with Motherboard. The screenshots mostly contained personal information such as email addresses of a handful of specific Roblox players, but some of them included high profile users such as the YouTuber Linkmon99. Linkmon99 is well known in the Roblox community for being the "richest" Roblox player in the world in terms of limited in-game items."That email address is the one secretly linked to my account," Linkmon99 told Motherboard when presented with the exposed personal information and asked if it was genuine. Linkmon99 said that on Thursday they received a message from the hacker containing the email address linked to his account, and "I knew it must be true because there's no other way anyone else could have found that email or other private info that was attached regarding my moderation history, account status, etc." The email address was designed to be private and created specifically just for his Roblox account after his account was previously hacked, Linkmon99 told Motherboard.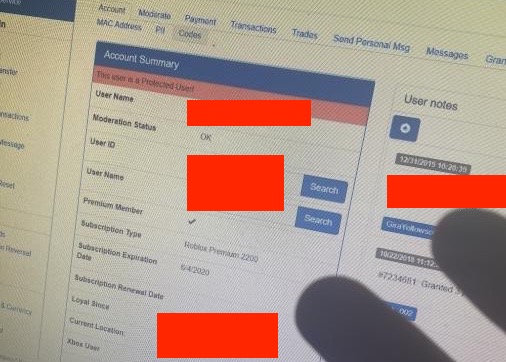 Beyond just viewing user data, the hacker was able to reset passwords and change user data too, according to screenshots of the customer support panel the hacker shared with Motherboard. The hacker said they changed the password for two accounts and sold their items. One of the screenshots appears to show the successful change of two-factor authentication settings, an extra form of security beyond just a password, on an account, with the panel reading, "Two Step Verification settings updated."A Roblox spokesperson told Motherboard in an email, "We immediately took action to address the issue and individually notified the very small amount of customers who were impacted."The hacker said they first paid an insider to perform user data lookups for them, and then targeted a customer support representative themselves. The hacker provided a series of screenshots showing alleged communication between them and the insider; on LinkedIn, this worker is listed as having worked as an in-game support contractor for Roblox.The hacker also attempted to claim a bug bounty from Roblox, they said. Legitimate security researchers often identify vulnerabilities in sites or services and then report those issues to the respective company so the problem can be fixed; companies then pay the researchers in response. The request of the hacker, who appears to have acted more maliciously than a legitimate security researcher, was denied.
Beyond just viewing user data, the hacker was able to reset passwords and change user data too, according to screenshots of the customer support panel the hacker shared with Motherboard. The hacker said they changed the password for two accounts and sold their items. One of the screenshots appears to show the successful change of two-factor authentication settings, an extra form of security beyond just a password, on an account, with the panel reading, "Two Step Verification settings updated."A Roblox spokesperson told Motherboard in an email, "We immediately took action to address the issue and individually notified the very small amount of customers who were impacted."The hacker said they first paid an insider to perform user data lookups for them, and then targeted a customer support representative themselves. The hacker provided a series of screenshots showing alleged communication between them and the insider; on LinkedIn, this worker is listed as having worked as an in-game support contractor for Roblox.The hacker also attempted to claim a bug bounty from Roblox, they said. Legitimate security researchers often identify vulnerabilities in sites or services and then report those issues to the respective company so the problem can be fixed; companies then pay the researchers in response. The request of the hacker, who appears to have acted more maliciously than a legitimate security researcher, was denied.
Advertisement
Roblox is available across PC, Xbox, and mobile devices. Users can create their own games with their platform's engine or play others' creations. Roblox also leans heavily into microtransactions, with users able to buy game-passes to access more powers and abilities, or they can purchase cosmetic items for their character with in-game currency. Roblox game developers can also cash-out and earn real money from their creations.The game is especially popular with children, with a vibrant YouTuber community around the game, and families are using the platform for playdates and parties during the coronavirus pandemic.Do you work at Roblox, or have any insight into how users make money on the platform? We'd love to hear from you. You can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
Advertisement
Advertisement

Advertisement
Originally the hacker told Motherboard they phished a Roblox worker to gain access to the back end customer support panel, before backtracking and claiming it was due to an issue in a piece of authentication software. There is no indication such a vulnerability existed. Roblox characterized the hack in an email to Motherboard as a social engineering attack, which would be inline with phishing."We’ve also reported the actions of this individual to HackerOne for investigation as an additional measure," the Roblox spokesperson added in their statement, referring to the bug bounty platform that Roblox uses to field potential bounties from researchers.The hacker said they changed the password for and stole items from Roblox users once they "had a feeling the bounty shit was gonna go south."Targeting customer support representatives can be an effective method for hackers to access user data. Last year a hacker compromised a Microsoft customer support account; Microsoft did not admit the hacker could then read the email of any non-corporate Hotmail, Outlook, or MSN account until Motherboard found evidence of the access and confronted the company.As Motherboard has previously found, scammers also pay insiders at telecom companies to perform SIM swapping attacks, where the employee ports a target's mobile account over to a SIM card the hacker controls, allowing them to then trigger password resets on various accounts or receive two-factor authentication codes.Subscribe to our cybersecurity podcast, CYBER."I did this only to prove a point to them."
