Remnants of that hack still exist today, and can be found in Twitch source code stolen and dumped on the internet by hackers last week in another major data breach that exposed the revenues of streamers on the platform as well as internal source code. Twitch has changed significantly since 2014, but former employees say that the earlier hack had knock-on effects that can still be seen today.Outside of the company, Twitch did not disclose details of the breach, nor its extent. Twitch's users would only find out about the breach six months after its discovery, on March 23, 2015, when the company published a short blog post that explained "there may have been unauthorized access to some Twitch user account information," but did not let on nearly how damaging the hack was to Twitch internally.“The hackers had such wide access before they were detected, we basically had to rebuild everything from scratch”
The random food name generator Twitch developers wrote after the 2015 hack. This code was leaked as part of the 2021 incident. (Image: Motherboard)
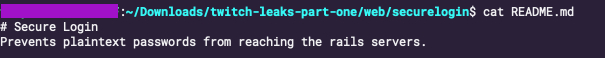
When Twitch finally disclosed the hack in March of 2015, security engineers at Twitch and Amazon, who had come to help with the incident response, concluded that the hack had started at least eight months before the discovery in October of 2014, though they had no idea if the hackers had actually broken in even earlier than that, according to the former employee. "That was long enough for them to learn entirely how our whole system worked and the attacks they launched demonstrated that knowledge," the former employee said."The hackers had such wide access before they were detected, we basically had to rebuild everything from scratch," the former employee added. "Some of the response involved rewriting the login process because the hackers had figured out how to send a copy of every single user's password to their servers. They also gained access to all of our source code and all of our databases."Do you work at Twitch? Do you have more information about the recent breach and leak? We’d love to hear from you. You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, Wire/Wickr @lorenzofb, or email lorenzofb@vice.com.
When the former Twitch employees who spoke to Motherboard found out about the leak, some were surprised, and others weren't. "When I heard this, I really wondered how they could be so sloppy, especially with Amazon as parent," one of them said.“In the earlier days of Twitch the security team had a presence, but they seemed to be stretched to the limit”

